What is blockchain? Many people have heard of it as it is one of the fastest growing information security technologies of the past decade, but many people may not know what it is or how it is used. Particularly for business applications. Originally developed for record keeping for cryptocurrencies, like Bitcoin, blockchain is a new way for users to store their data and keep it visible to the public without it being corrupted. If it does not make sense at first, do not worry; it is much less complicated than it seems.
What is Blockchain?
According to Don and Alex Tapscott, authors of Blockchain Revolution, “Blockchain is an incorruptible digital ledger of economic transactions that can be programmed to record not just financial transactions but virtually everything of value.” Put simply, blockchain is a distributed, decentralized, and public ledger that stores information regarding transactions or other data. It was discovered by a person or group under the pseudonym Satoshi Nakamoto and was originally designed for data protection.
EDI is common in today’s business climate with over 85% of all electronic business transactions using it. It is often used with…
Blockchain is distributed, meaning that the data is stored across a complex and difficult to enter network of thousands (or millions in the case of Bitcoin) of computers called “nodes. It is decentralized because no single node stores master information that can be manipulated. The entire chain is identical and each change made to it affects each copy on each computer simultaneously. This also makes it very difficult to hack in and alter data. It is a public ledger as each user is able to see the transactions in progress and each user has the same data. The transaction data is also transparent and can be viewed by anyone from specific blockchain sites.
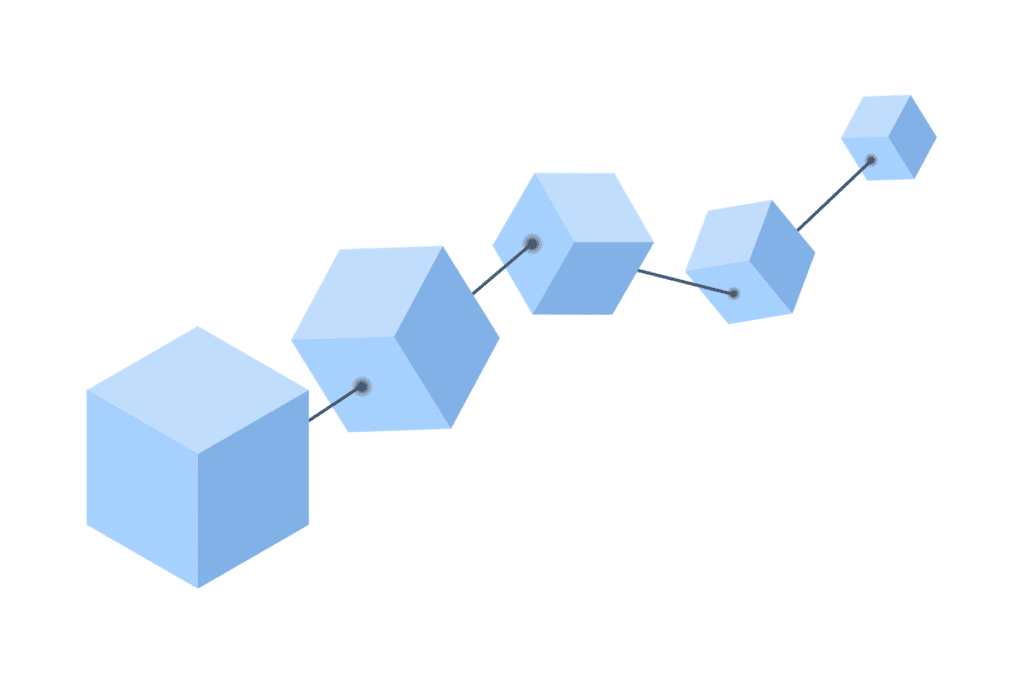
The system is named blockchain because it is literally a chain made from blocks of information. Digital information (block) is added to a public database (chain) in measured amounts of 1MB or less, stretching out practically endlessly. Each block consists of three parts:
1. Information about transactions – the date, time, and dollar amount of a transaction.
2. Information about who participates in a transaction – the user ID of the person receiving money or service.
3. Information that distinguishes each block from one another – a unique code called a “hash” made of letters and numbers.
Each block is also connected to the next block in line by the hash.
How Does Blockchain work?
Blockchain works like a spreadsheet that is duplicated across thousands of computers at one time and regularly updates if any changes are made. Much like a Google Doc as opposed to an Excel spreadsheet. With the Google doc, several users can open the page and manipulate data at the same time, but the page is the same for each user in the document.
With the old way of storing data, like using an Excel spreadsheet, a user would send the data directly to whomever needed to make changes and that user would need to return the changes to the original sender. If multiple people needed that information, each would need to be sent a copy of the updated information or there would be confusion with the data. The confusion from the old way gave an opening to blockchain. Its records are public, easily viewable, easily verifiable, and it cannot be corrupted.
When a user wants to store information, they must create a block. For a user to add block to the chain four things must take place.
1. A transaction must occur – This can be a purchase, sale, or any other information addition.
2. A transaction must be verified by the network of computers – a security measure called a consensus mechanism must verify the block addition and approve if it can be added to the chain.
3. The transaction is stored on a block – After it is verified as accurate.
4. The block is given a hash – A hash is a unique name and identifier for the block. It connects to the block following it.
Hashes look like this:
First, there is a block of information.

This block is given the Hash “BL76”. So, when Block 2 is created, it will look like this:

Block 2 has unique information combined with the information from Block 1 (BL76). Now, Block 1 and Block 2 are connected by the Block 1 hash, and Block 2 will be given its own unique hash “PS24”. When a third block is added, it will look like this:

Block 3 combines new data with the data from the previous blocks before it and each block after will follow a similar pattern. Blocks can be added to the chain endlessly like this and users are always notified when a block is added.
This is why it is difficult to manipulate data maliciously. Any change made to Block 1 changes the hash.

This block would now be called YZ82 and no longer connects with Block 2 or any of the other blocks on the remainder of the chain. Breaking the chain makes it easier for other users to see that the information has been tampered with. The system will know something is wrong and automatically reject the change. After that, it reverts to a previous record where all of the blocks are chained together.
It is technically possible for a hacker to corrupt the data; however, it is highly improbable because of the significant difficulty. A hacker would need to have the computing power to change each subsequent block in the chain to match the changed block AND convince 51% of the nodes that the change is legitimate. Often there are thousands (if not more) blocks in a chain, and changing each block would take time. So, the hashes work as a protection feature as much as a detailing feature. Another protection process is constant data reconciliation.
Information in blockchain is shared in a continually reconciled database by processes called consensus mechanisms. Consensus mechanisms are rules that govern who can contribute and participate in the blockchain. One of the most popular consensus mechanisms for cryptocurrencies is called Proof of Work – a complex math problem the computer must solve to be given access to the chain. These problems are difficult and the odds of a computer solving them are 1 in 7 trillion. So, a user must have an incredibly high-powered, often expensive, computer in order to manipulate data.
The reconciliation process takes place every ten minutes and the data on each computer is updated. If there are any conflicts in the chain (two similar chains but one is longer) the chain that is the longest is accepted.
Is Blockchain Secure?
The simple answer is yes – blockchain is secure. When users store their data across a decentralized network, it eliminates the threats that systems with a centralized point of vulnerability experience. Hackers are not able to manipulate the data in the same way because of the public access and ability to scrutinize data integrity. Users can see where mistakes are made and will not allow them to join the chain. Any other malicious actions are eliminated due to reconciliation measures.
Blockchain uses a sophisticated encryption method to protect its data. Individual users wanting to access their data have a digital wallet made up of two keys – a public and a private key. These keys are codes that are given to a user when they initiate their first cryptocurrency transaction. Both are unique and can be user identifiers.
• Public Keys – are long, randomly generated strings of numbers (cryptographic codes) that allow users to receive cryptocurrencies into their account. These allow users to send transactions to the distributed network of nodes to be verified. A public address is a shortened and compressed version of the public key and acts as a destination for users to send currency – like a bank account. Ex. A school locker.
• Private Keys – are unique personal IDs for users to approve transactions. They act like a digital signature. Ex. A combination for the school locker.
These keys are both a security and privacy measure. Nobody can access User 1’s data or currency without User 1’s Private Key and nobody knows User 1’s true identity. They only know him by his Keys. Other users could discover User 1’s Public Key and Public Address if they had access to User 1’s Private Key, but that only works one way. It is impossible for users to determine User 1’s Private Key number from his Public Key. If User 1 loses his Private Key, he loses all access to his currency and data, but if he loses his Public Key, it can be recreated from the Private Key.
These measures, along with the consensus mechanisms, make it very difficult to alter or steal data. Having the data decentralized makes changing all of data simultaneously difficult as well. So, overall blockchains are secure.
Is Blockchain Private?
Blockchains offer their users privacy as well. Despite blockchains being public ledgers, users are offered anonymity through the digital wallet. User’s personal identities are disguised by their private keys. When transactions take place, users would be provided with a username or digitally coded name as opposed to their specific information.
Real World Applications
Primarily, blockchain was developed as the record-keeping database behind Bitcoin, but since its creation has found applications in many businesses. For instance:
• Smart Contracts: These are the way of the future. Users are able to code simple contracts that will execute when specific conditions are met. Ex. In logistics, a smart contract could be developed to pay a carrier for a shipment after the shipment has been delivered, a proof of delivery signed, and documentation uploaded to the shipper’s database. Each condition must be met to receive payment.
• Sharing Economy/Uberization: These could be direct peer-to-peer payments without using either cash or a third party application like a credit card, credit card reader, or user interface like Uber, AirBnB, etc.
• Crowdfunding: Users can directly fund projects they are interested in without going through brokerages or stocks.
• Government: These can be used for elections as it is incredibly difficult to forge an identity or manipulate the polling results.
• Logistics: Blockchains can be used to verify information like locations, dates, times, and product codes. Users can have exact time/date stamps available as well as location. Each party would have exact evidence to prove a shipment delivered at a particular time or that a product originated from where the shipper said it did.
Advantages/Disadvantages
The blockchain technology is not a one size-fits all solution for each company and often it acts like a two-edged sword. For instance:
Cost:
• Advantage: Users can save a significant amount of money by not working with third party verification administrators (apps, notaries, brokers) and the costs that go with them. Also, businesses could save on credit card transaction fees.
• Disadvantage: The costs of computing consensus mechanisms and proofs is incredibly high. Users need high powered computers capable of solving the algorithms as well as the energy involved in powering and cooling the computers.
Security:
• Advantage: Blockchains require transactions to verified before they are recorded. Also, each block that is recorded has unique identification to protect from tampering. The technology is open source and transparent, so the correct changes can be made when needed, but no other changes.
• Disadvantage: Central banks like the US Federal Reserve would not be able to use this technology as they are unable to control its currency. This technology would only be able to exchange non-governmental currencies like Bitcoin. This makes it difficult for the average user as they may or may not be able to exchange in cryptocurrency.
Privacy:
• Advantage: Users can access public details such as transaction history, but they do not have access to other user’s personal information unless they have that user’s Private Key.
• Disadvantage: The privacy encourages illegal trading and activity. Also, if users do not maintain their digital wallet, they can lose all of their data and cryptocurrency.
Decentralization:
• Advantage: Having the information spread across the network makes it difficult to tamper or modify.
• Disadvantage: May not be suitable for industries where centralization is necessary. (Areas like medical records or national banks)
Efficiency:
• Efficiency: Blockchain works 24/7 so transactions can be processed quickly.
• Inefficiency: Some systems can only process about seven transactions per second whereas classic systems can process 24,000.)
Other Advantages:
• Accuracy: Each transaction is verified by thousands or more computers. Errors would be evaluated and eliminated before being added to the chain.
Other Disadvantages:
• Susceptibility: Blockchains can be altered if they can influence 51% of the computers in a network. It is currently viewed as improbable but not impossible.
Blockchain is one of the fastest growing information security technologies today. It is a distributed and decentralized system that offers speedy transactions and superior data security. Also, it is a public ledger offering transparency and strict verification all while protecting users’ privacy. Though it was developed to support cryptocurrency, it has found applications in other businesses through areas like smart contracts and peer-to-peer transactions. Now that blockchain has been it explain, how can you implement it into your business?